Security Control Planning
Baseline Information
Founded in 2010, Widget Inc. develops and sells the famous “Beeplepop” along with a line of household innovations that forever revolutionized the way we live and work. Widget Inc. main office is located at an office park in St. Louis, MO, and accommodates approximately 100 full-time employees. The office park is home to 3-4 similarly sized companies with shared parking facilities.
At Widget Inc., there are five (5) primary business units that report directly to the CEO:
Office of the Controller - Manages all of the finances of the organization including the general ledger, accounts payable, and accounts receivable. This office is divided into two primary offices: HR, Accounting
Operations - Manages the distribution center and order fulfillment. This office is further divided into two primary workgroups: Processing, Inventory Control
Research & Development - Manages the highly sensitive intellectual property for the company, including any patent applications as well as the design team of the “Beeplepop” and ancillary product lines and prototypes. There are two primary divisions of this office: Product Management, Technology Transfer
Sales & Marketing - Manages the website and social media presence. This office also oversees territorial sales and customer satisfaction of the product and is divided into three offices: Web Development, Communications, Account Management
Information Technology - Manages the technology resources of the organization which includes, but is not limited to: endpoint computing, network infrastructure, and business applications. These are supported by the following offices, respectively: Help Desk, Infrastructure, Business Systems
Facilities management and house-keeping services are outsourced to a third-party.
Technology Overview
Widget Inc. maintains an on-premise data center with dedicated hardware running its entire infrastructure. A high-level network topology diagram is provided in the zip package. Descriptions of the major components in the infrastructure are outlined below.
Widget Inc. core infrastructure consists of a series of routers and switches that segment the network into virtual local area networks (vLANs) that are designated by subnets with non-routable IP addresses. These non-routable IP address ranges are denoted by the blue boxes. The network topology and access control lists were originally designed by a Network Engineer who left the company in 2012, but have since been maintained by a Systems Administrator. The current Access Control Lists (ACL) for these vLANs are designated by the green boxes. (See below: Widget Inc. - Network Diagram - Figure 1).
Key Applications:
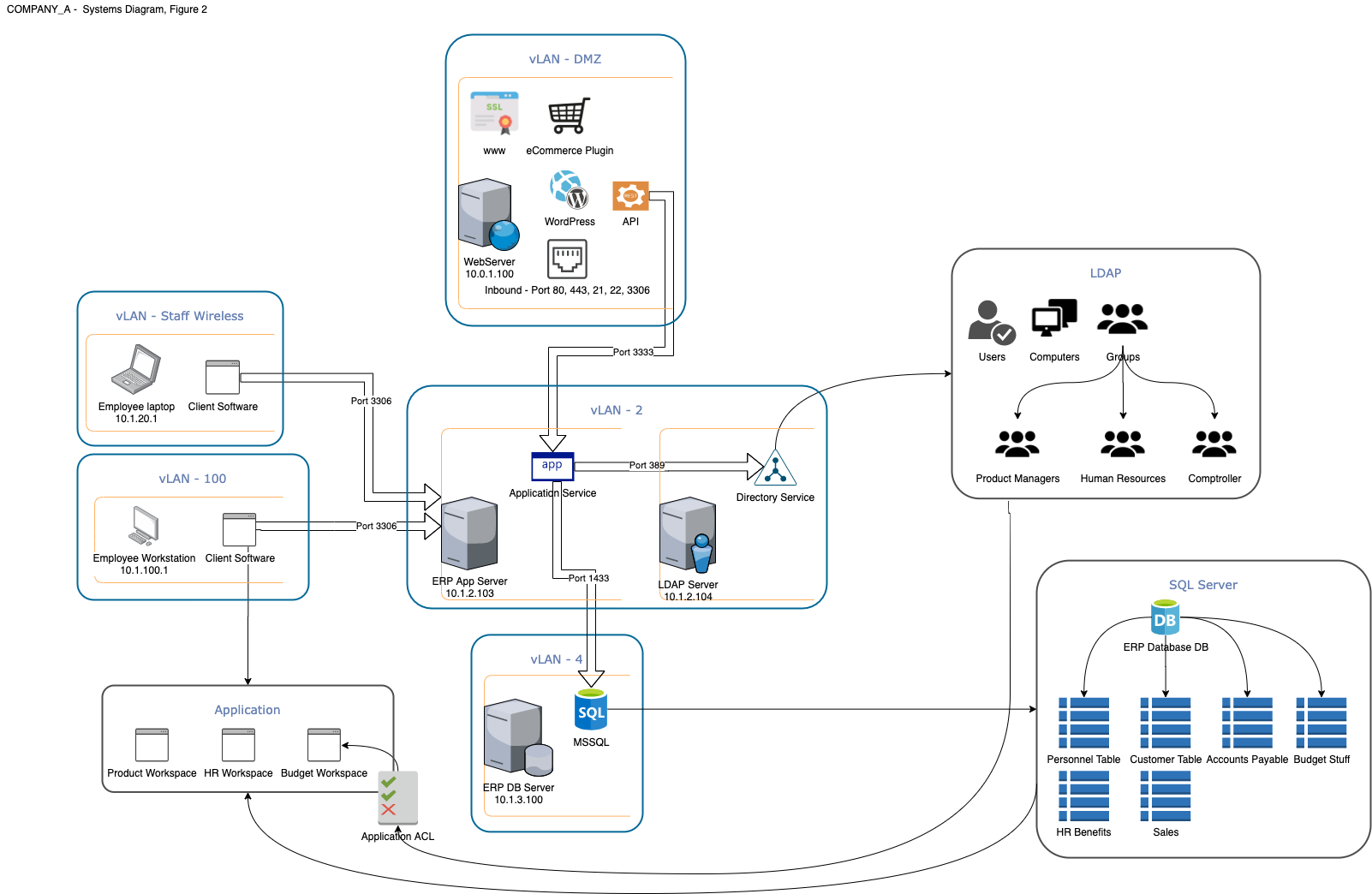
Widget Inc. primary web property (www) is an eCommerce website, built on WordPress. The customer-facing website is currently secured with an SSL certificate from a well-known Certificate Authority. The eCommerce platform serves as the company’s point-of-sale and handles payment card processing. It also communicates to the Enterprise Resource Planning (ERP) system through an Application Programming Interface (API) (over port 3333) using an application-specific service account which updates the customer database and financial tables. The server that hosts the primary website is a standalone server located in the company’s demilitarized zone (DMZ).
Widget Inc. ERP system contains highly sensitive information including all financial information for the company and customer information and is used to generate all of the business intelligence for the senior executives. The ERP system is a three-tier application which includes client software that is installed on employee workstations which communicate with the ERP App Server (over port 3306). The ERP App Server’s underlying database is hosted on a dedicated ERP Database Server running MSSQL which uses built-in service accounts to perform reporting and maintenance functions. The ERP system utilizes Widget Inc. LDAP service for identity management and user account control via LDAP groups. Users are automatically provisioned in LDAP (over port 389) by an automation process within the ERP which generates unique UIDs for staff. LDAP authentication is based on username and password. The ERP system was implemented in 2015. Prior to this time, Widget Inc. maintained customer, budget, and personnel with a series of Excel spreadsheets. Due to legal reasons, Widget Inc. is obligated to retain this legacy data. (See below Widget Inc. - Network Diagram - Figure 2).
In 2018, the company added a wireless LAN topology to accommodate users bringing their own devices to the office, which includes a Guest Wireless network for the front lobby. Widget Inc. utilizes a RADIUS server to perform network-level authentication for staff and/or company-owned computers connecting to SSID: STAFF_NETWORK. The RADIUS server performs user-lookup against the LDAP server (over port 389). GUEST_NETWORK does not require authentication. (see below Widget Inc. - Network Diagram - Figure 3).
Widget Inc. maintains a network fileshare that contains folders that correspond to each of the departments and workgroups. The department folders may contain sensitive information that includes, but is not limited to: customer data, product information, trade secrets, and salary data. Fileshare folders are created by request. Access to folders is granted by request and in some cases with discretionary access control methods (DAC). (see below Widget Inc. - Network Diagram - Figure 4).
My Objectives
You have been recently hired by Widget Inc. as an information security analyst working for the infrastructure team. You are the only staff member whose role is dedicated solely to information security. You report to the Manager, Infrastructure who reports to the Chief Information Officer (CIO). Other members of the infrastructure team include 1x Systems Administrator, 1x Network Engineer (vacant), 1x Application Administrator/Programmer, 1x Telephony Engineer.
Your primary responsibilities are to Protect, Detect, and Respond to possible threats to the security of the organization’s mission. These duties include:
Install security measures, including firewalls and data encryption programs
Monitor for security issues
Investigate and document security breaches and other incidents
Detect and fix potential vulnerabilities
Stay up-to-date on IT trends, news/events, and security standards
In addition to these primary responsibilities, you are also responsible for providing Consultation and Training:
Research security enhancements and make recommendations to management
Inform colleagues about information security management
Develop company-wide security best practices
Securing personnel (the human asset) is your highest priority.
Results
During the process, I created several documents that could be shared with upper management with a variety of information that can be useful in protecting the systems and improving security posture. The documents include:
NIST Workbook Solution - This document contains an assessment of the current security posture at Widget Inc. as well as comments about the different NIST standards.
Security Plan Solution - This contains several different possible solutions to improving the secuirty posture with suggested integrations and recommendations to hardening security.
Deployment Plan Solution - This document contains a variety of information about deploying several different suggestions in the Security Plan Solution document in order to effectively impliment the security hardening
Network Diagram Solution - This document is a visual representation of what logical controls should be implimented as well as where in the network they should implimented to effectivley improve security.